How to run Ostinato in a ssh-only environment
Ostinato has a controller-agent architecture that uses a TCP connection (on port 7878 by default) for communication between them for command and control.
One popular deployment of this architecture is where the agent runs on a headless server and connects to the DUT via direct ethernet links. Both the DUT and server are co-located in a lab. The GUI controller on the other hand runs on users’ laptop or desktop which is on the corporate network and different from the lab network. For the agent and controller to be able to talk to each other they need to be able to talk TCP over port 7878 (or another user specified port) between these two networks.
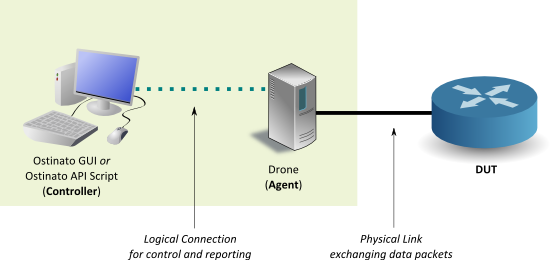
Some environments may not allow any communication between these two networks except ssh (tcp port 22) which leads to a problem in running Ostinato.
To enable Ostinato agent-controller communication in this restricted environment, one can use ssh tunnelling.
Assuming you are running the agent (drone) on host bar and the Ostinato controller GUI on host foo, run the following command on foo -
foo$ ssh -L 7878:localhost:7878 bar
The above command will create a local server on foo listening on port 7878 and any TCP traffic to this port will be transparently tunnelled to bar:7878 over ssh. The tunnelled traffic will be encrypted as well which should be enough to bypass most firewalls.
Now on foo, when you open the Ostinato controller GUI, the 127.0.0.1 local portgroup will try to contact the local server running on foo:7878 which in turn will contact the agent running on bar:7878.
If you want to learn more about ssh tunnelling, SSH Tunnelling explained is a good read.
Interested in more Ostinato tips and tricks? Subscribe to receive email updates!
Leave a Comment